A self-signed certificate is a certificate that is signed by the same entity that created it, using its private key, without the involvement of a trusted certificate authority. This guide
security
Privileged Access Management (PAM) is a crucial aspect of cybersecurity that focuses on safeguarding and controlling access to an organization's most sensitive information and resources. At its core, PAM is
HTTP is an application layer protocol used to access web content from and push web content to a web server which is stateless in nature. HTTP flood attack is a
Everything in the world has advantages and disadvantages. It is not an exception for email usage in the workplace because it could help and encourage employees to abusive things. Thus,
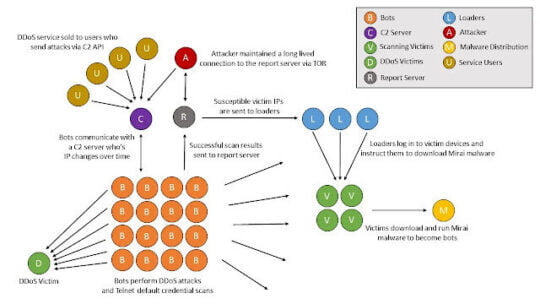
Hackers are fast, 'invisible’ and the damage that they cause cannot be undone. They can search your website within no time and get crucial information that may even compromise your
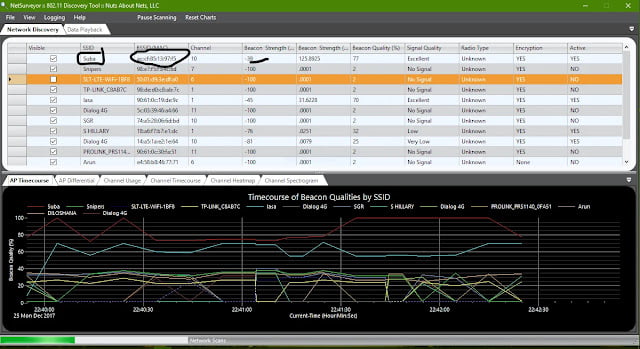
1. WIFI discovery In Wi-Fi discovery, we do have to find some information about mac address, channel number, and ssid, signal strength, a security protocol. This information is available in
Load More