How does site to site ipsec vpn work
IPsec is a network protocol suite which consists of multiple protocols to secure the data over public network. for example AES or 3DES for encryption and MD5 or SHA for integrity . IPsec uses symmetric key encryption algorithm for encrypting the data. symmetric key means same key which is used for both encryption and decryption which is high efficient and less work load compare to asymmetric key encryption algorithm .
The problem with symmetric key algorithm is both peers should need to have the same key and the key should not be sent over public network because hacker can easily eavesdropping the key packet and decrypting the data and AES or 3DES do not create or exchange keys for themselves. to overcome the this problem symmetric key should be set manually on both peers but it is not good in the view of security so they have implemented a protocol name Diffie Hellman, it will generate shared secret key without actually sharing the exact shared secret key between two peers. it has to go through 2 phases for the successful data packet transmission.
phase 1
phase 1 is for secure internet key management and create secure channel for phase 2 negotiation .
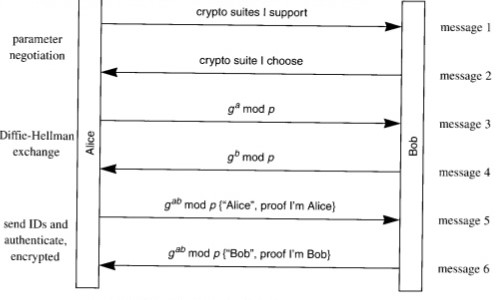
without phase 1, phase 2 negotiation will not happen anyway. ikev is a hybrid protocol which made from ISkamp , Oakley and Skeme. it uses UDP port number 50. phase 1 has two modes such as main mode and aggressive mode. main mode is the default mode. main differences between main mode and aggressive mode are anonymity and no of messages for phase 1 completion . main mode keeps anonymity while other mode does not. main mode uses 6 messages to complete phase 1 but aggressive mode uses only 3 messages. main mode and aggressive mode are applicable for only IKEV1 .
main mode
As shown in the above diagram , first 2 messages are for security associations negotiation such hashing, authentication, Diffie-Hellman Group value, life time and encryption. other two messages for generating shared secret key and final two messages for authenticating peers. final two messages encrypted because now both peers have shared secret key so they can use it for AES or 3DES as symmetric key.
Aggressive mode
As shown in the above diagram, first 2 messages are for security association negotiation, generating shared secret . and final 2 messages are for authentication. once authentication is successful, phase 1 tunnel will be up.
Phase 2
it has only quick mode. phase 2 tunnel will only form if phase 1 has been already formed. authentication no need and regenerating shared secret key is optional. IPsec uses 2 encapsulation type, ESP and AH. ESP provides confidentiality to the data but AH does not. AH provides integrity up to some IP header parameters. both do not rely on TCP or UDP. ESP protocol number 50 and AH protocol number 51. SO both have problem with intermediate device which is doing NAT (network address translation) . NAT does require TCP or UDP port otherwise it will drop the packet.especially NAT traversal is used to over come this problem. NAT traversal is nothing but adding UDP header with port 4500. for more information read IP Security (IPsec) and Internet Key Exchange (IKE) Document Roadmap
Quick mode
Configuring Site To Site IPsec VPN On Cisco ASA 5505, 5510, 5520, 5515X, 5525X, 5540X, 5545X, 5550X.
VPN termination peers and pcs have full connectivity. ICMP is inspected on both Cisco ASA Firewalls. Routers R3 and R4 are doing port address translation. NAT exemption is configured on both routers for VPN traffic.
Basic configuration- PAT Exemption
ACL should be created with two statements. first statement will disable PAT process for the ICMP traffic which is from source 192.168.1.0 to 192.168.2.0 (Lan To Lan vpn traffic.). Second statement will allow pat process for internet traffic. for R4 source and destination will change.
R3
ip access-list extended nat
deny icmp 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
permit icmp 192.168.1.0 0.0.0.255 any
ip nat inside source list nat interface Serial3/0 overload
R4
ip access-list extended nat
deny icmp 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
permit icmp 192.168.2.0 0.0.0.255 any
ip nat inside source list nat interface Serial3/0 overload
VPN configuration ASAV-1
firstly, we do have to enable ikev1 on outside and define the 5 parameters.
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 5
lifetime 86400
Transform-set should be configured for phase 2 negotiation. sha-hmac is adding unique key with data to the sha hashing algorithm so it provides better security.
crypto ipsec ikev1 transform-set vpntrans esp-aes esp-sha-hmac
ACL should be configured to match the VPN L2L traffic. you should configure it according to your requirement.
access-list vpntraffic extended permit icmp 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
This ACL only allows the remote lan network hosts to enter outside interface of the asav-1.
access-list outside-in extended permit icmp 192.168.2.0 255.255.255.0 any
access-group outside-in in interface outside
Crypto map should be defined and it should include ACL to match VPN traffic, peer IP address, transform-set name which is configured earlier. Name is case sensitive. setting pfs is optional but it is commanded in the security perspective. if you enable pfs then new shared secret key will be created for encryption algorithm.
crypto map map1 1 match address vpntraffic
crypto map map1 1 set peer 172.16.2.1
crypto map map1 1 set ikev1 transform-set vpntrans
crypto map map1 interface outside
Below commands are different from ios to Asa. Pre-shared key should defined under tunnel-group. for ASAV-2 few things should be change like ACL, peer ip address.
tunnel-group 172.16.2.1 type ipsec-l2l
tunnel-group 172.16.2.1 ipsec-attributes
ikev1 pre-shared-key cisco12345
ASAV-2
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 5
lifetime 86400
crypto ipsec ikev1 transform-set vpntrans esp-aes esp-sha-hmac
access-list vpntraffic extended permit icmp 192.168.2.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list outside-in extended permit icmp 192.168.1.0 255.255.255.0 any
access-group outside-in in interface outside
crypto map map1 1 match address vpntraffic
crypto map map1 1 set peer 172.16.1.1
crypto map map1 1 set ikev1 transform-set vpntrans
crypto map map1 interface outside
tunnel-group 172.16.1.1 type ipsec-l2l
tunnel-group 172.16.1.1 ipsec-attributes
ikev1 pre-shared-key cisco12345
Security associations verification commands
show crypto ikev1 sa detail
show crypto ipsec sa detail